Rto - An Overview
Wiki Article
Some Known Questions About S3 Cloud Backup.
Table of ContentsThe Only Guide to Ec2 BackupAws Cloud Backup Can Be Fun For AnyoneThe 4-Minute Rule for Aws S3 BackupSee This Report on Ransomware ProtectionSome Known Questions About Rto.
Keeping numerous vendors and also systems along with typical computer has placed fantastic pressure on IT divisions. Moving forward, information security need to be able to adapt to these currently complicated circumstances. Data protection techniques are created to protect information, protect privacy and also avoid data loss and corruption without trading them for analysis as well as testimonial.
Data erasure methods also verify the information can not be recuperated. Gain access to management manages make sure data honesty by restricting accessibility to digital properties. This allows granular control over which groups of people are granted access to systems, as well as when. Monitoring as well as safeguarding endpoint gain access to expands the reach of a data protection program by covering network-connected devices regardless of where they are situated.
So a lot of the globe's communications and business happens in the cloud or through personal devices in remote job atmospheres. The finest data defense solutions combine robust security steps with human procedures and workflows. The total goal: to ensure information protection is considered early throughout the digital details life cycle.
9 Easy Facts About Aws S3 Backup Explained
Information safety and security is everyone's service, so, it's also crucial to ensure routine, ongoing safety recognition training is component of your information protection strategy - aws backup - https://www.merchantcircle.com/blogs/clumio-atlanta-ga/2022/11/Some-Known-Details-About-Data-Protection/2336789. Freelance Modern Technology Author Michelle is an independent modern technology writer. She has developed technical content for a variety of brands and also magazines, consisting of Organization Insider, DICE, GE Dig ...The terms data protection and data privacy are frequently used reciprocally, however there is a vital difference in between both. Information personal privacy specifies who has access to data, while data security gives devices as well as plans to in fact limit access to the data (https://www.directorynode.com/author/clumi0/). Compliance guidelines aid make certain that user's privacy requests are brought out by business, as well as companies are responsible to take measures to protect personal user information.
It plays a vital duty in company procedures, development, as well as finances. Data security remedies rely on technologies such as information loss avoidance (DLP), storage with built-in data security, firewall softwares, encryption, as well as endpoint defense.
An information security strategy is crucial for any kind of organization that gathers, handles, or shops sensitive data. Information defense concepts aid protect data as well as make it offered under any type of scenarios.
Some Known Incorrect Statements About Aws Cloud Backup
Below are vital data monitoring facets relevant to information security: making certain customers can access and use the data needed to carry out business also when this information is shed or harmed. entails automating the transmission of crucial information to offline and online storage. includes the assessment, cataloging, and also protection of details assets from different resources, consisting of center failures and also disturbances, application and also individual errors, equipment failure, as well as malware and virus assaults.Information personal privacy is typically applied to individual health and wellness information (PHI) and directly identifiable information (PII). Data personal privacy concerns use to all delicate information that organizations deal with, consisting of that of clients, shareholders, as well as employees.
It stops bad guys from being able to maliciously utilize information and assists guarantee that companies fulfill governing needs. Information defense policies govern exactly how specific information types are accumulated, transferred, and made use of. Individual data consists of different kinds of details, consisting of names, photos, email addresses, bank account information, IP addresses of desktop computers, and biometric information.
Things about S3 Cloud Backup
Additionally, each regulation includes countless clauses that may put on one situation yet not another, as well as all regulations go through adjustments. This level of intricacy makes it challenging to apply conformity continually and appropriately. Although both data defense as well as personal privacy are important and the two commonly come together, these terms do not represent the same point.Data personal privacy specifies the plans that information security devices as well as processes utilize. You can limit accessibility with data protections while still leaving delicate information prone.
For defense, it is up to the companies handling data to make sure that it stays exclusive. Compliance guidelines reflect this distinction and also are created to assist guarantee that individuals' privacy demands are passed by firms. When it pertains to safeguarding your data, there are several storage and also management choices you can select from (s3 cloud backup).
Right here are a few of one of the most frequently used techniques and innovations: a very first step in information defense, this entails uncovering which information collections exist in the company, which of them are service essential and also which has delicate information that could be based on conformity regulations (aws backup). a collection of methods and also devices that you can make use of to stop information from being swiped, lost, or inadvertently erased.
All about Protection Against Ransomware
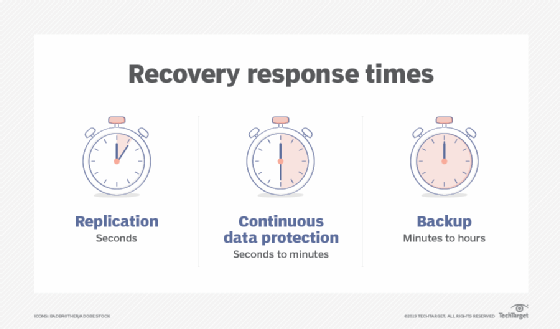
contemporary storage space devices provides built-in disk clustering as well as redundancy. For instance, Cloudian's Hyperstore provides up to 14 websites nines of durability, low price making it possible for storage space of large volumes of information, and also fast accessibility for minimal RTO/RPO. Discover more in our overview to. creates duplicates of information and stores them independently, making it possible to restore the information later on in instance of loss or alteration.Report this wiki page